The Internet of Things (IoT) is undeniably the wave of the future. Equipping devices from cars to refrigerators to thermostats with sensors and the ability to transmit data and receive commands means being able to optimize and control every device in your life remotely.
The early days of IoT have been rough when it comes to security. Because most initial devices linked to the IoT were just sensors transmitting data, there was little-to-no security implemented. If you’re using IoT devices in your home or office environment, you need to understand the type of threats that they face and the several simple ways to ensure that hackers don’t invade your space.
Why do you need to Secure your IoT Devices?
Below are some of the serious threats facing IoT devices at homes and in offices.
1. Botnets
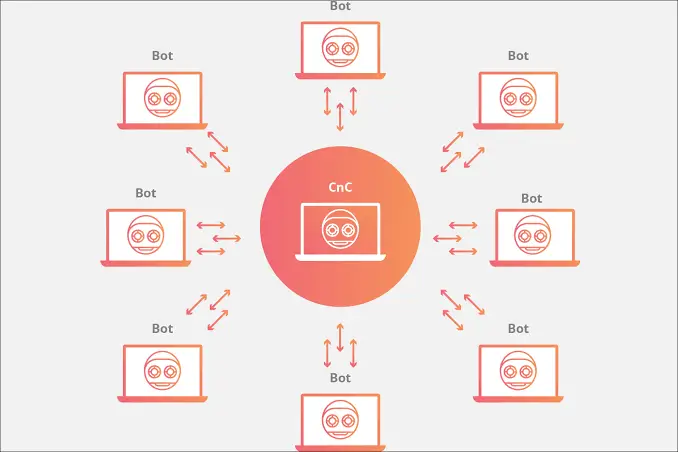
Botnets are networks comprising hundreds, thousands, or even millions of hacked devices that are remotely controlled by hackers. These hackers mostly take advantage of the poor IoT security implementation at the manufacturer level as well as at the user level to recruit them to their network. Once your IoT devices have been recruited, they can then be used to carry out malicious activities such as ad fraud, DDoS attacks, phishing scams, spams, etc.
2. Identity and Data Theft

IoT devices transmit a lot of data to carry out their tasks. This means that once hackers gain access to such devices, they can snoop on the traffic to try and obtain as much information about you or your organization as possible.
This information can then be used to carry out other, more dangerous attacks through social engineering. The hackers may then end up stealing your data or personal information. The attack itself can also be used as an entry point to your network and systems, which will facilitate them to obtain sensitive information.
3. Ransomware

Ransomware originates from the words Ransom Software, and it is a malicious piece of software meant to corrupt your devices until you pay a ransom. Since it’s relatively easy to infiltrate IoT devices, hackers can download malware to corrupt their operations and make the system unusable.
If the devices are within an enterprise, they can also use this opening to spread the ransomware to other systems through the network.
How to Bolster your IoT Security?
1. Change the Default Password to something difficult to guess
This is by far the most important IoT security measure.
All IoT-capable devices come with a default password. Legions of users never change said password because they don’t see it as a security risk. Hackers and cybercriminals are counting on people not changing the default password and can easily access any IoT device that doesn’t have a complex password.
This was well illustrated by the Mirai botnet, which scanned a huge block of the internet for devices that were using manufacture passwords or common custom passwords. The botmasters were able to recruit millions of devices, which were then used to make a DDoS attack on Dyn, a company that controls much of the internet’s domain name system (DNS) infrastructure. The attack rendered much of the internet almost inaccessible on the US East Coast.
2. Explore what makes a device “smart”
Things aren’t labeled “smart” because they can win prizes on a game show. That label comes from its ability to collect data and analyze it. Before you purchase a device, explore the kind of data that it collects and shares, how it is being used and stored, the efforts that are made to destroy it when it is done being used, and the impact such data will have in case of a security breach. Ensure that you are comfortable with all these.
3. Check each device’s website for Firmware Updates
Manufacturers regularly release firmware updates to boost security as well as to knock out potential security threats and glitches. It’s therefore important to frequently check your manufacturer’s website for updates or sign up for email notifications.
4. Use a Virtual Private Network (VPN) on your Home Network

A VPN will route all the data flowing from your home network through an encrypted tunnel to a secure server before sending it to the internet and on to its final destination. This encryption makes it impossible for any third party to see your data or where it is coming from.
To use a VPN on your home network, you need to configure it at the router level. Most ISP routers do not support VPN configuration, but you can buy a VPN-capable router. You can then set up a VPN of your choice manually or by flashing the router. There are tutorials for setting up your router on most VPN websites, but you can also go for a pre-flashed router with the VPN of your choice. These can be found at flashrouters.com.
5. Segment your Network
Most routers are capable of creating multiple networks, which is a good security measure to ensure that you have one connection for family members and another for guests. If your router has such a capability, consider creating a network dedicated to your smart devices.
This will automatically limit the accessibility of such devices, and the different connections will act as a buffer to prevent outside access to your data. It will also play an important role in case of a breach since the hackers will not be able to connect to other systems and devices.
6. Use IoT antivirus software to protect your network
Typical antivirus packages don’t cover IoT, but there are specialized ones like Bitdefender that provide blanket coverage. Such a comprehensive solution can safeguard against threats to IoT devices by detecting malware at the endpoint level point. It can also protect the whole network against other cyber-attacks by scanning your entire home network to look for vulnerable devices and passwords, then provide some security recommendations.
7. Disable UPnP
Most smart devices have a feature known as Universal Plug and Play (UPnP). The feature enables different devices to find and connect with each other. This provides a lot of convenience as you won’t have to configure each device separately. However, you need to be aware that the feature uses the local network for its functionality, and the network may be vulnerable to outside access. This also makes the devices vulnerable.
To prevent such vulnerabilities, disable UPnP on both your smart devices and your router.
8. Use Secure Network
Wearables can be easily exposed to threats since we all love that free WiFi at the restaurant, hotel, airport, etc. It’s important to note that most public WiFi hotspots are unsecured and are a haven for hackers. Once you connect to such a network, a hacker can easily hijack your device’s traffic and compromise the device.
It’s therefore important to avoid connecting your wearables or even your IoT apps to public networks. In case you have to connect your smartphone, ensure that you power up your VPN immediately.
9. Protect your Smartphone
Odds are your smartphone is the central hub for controlling your IoT devices. If you lose possession of your phone, even for a few minutes, you’re risking a seasoned criminal being able to pick up your phone and strip it of vital data and passwords in a matter of seconds.
You, therefore, need to ensure that your smartphone has all the necessary security measures to prevent unauthorized access to the apps or your data.
10. Be Cautious with the Cloud
IoT devices usually rely on the cloud for data storage, and most IoT providers offer the service for free. However, you need to understand that a lot of your data is being sent there. This data connection only works when you have an internet connection, and a breach of your connection security means that the data can be intercepted.
Apart from that, you may not have an idea of the form of security that the cloud provider has implemented to secure your data. Before you purchase a device, ensure that you go through the manufacturer’s privacy policy and look for assurances on the security implementations for data protection.
11. Read all about any IoT app you install on your Smartphone
Take time to read the terms and conditions before allowing any app access to the data on your smartphone. The more it gobbles up, the greater the risk of your personal and/or financial data getting exposed in the event of a hack to that device’s network.
12. Disable Social Sharing features on your IoT apps
Criminals love watching social media posts. They can reveal your location and often tell others when you aren’t at home. We’re not just talking about data hacks here, but home burglaries as well.
Conclusion
IoT connectivity is on the rise, and it is meant to make life more convenient and enjoyable. However, it also brings various security concerns due to poor security owing to the limited resources used in the devices. It’s therefore important to understand the security threats in the IoT world and take measures to ensure that you do not fall victim to such.
